How to Protect Your PC from the ZombieLoad Attack

Researchers discovered a set of frailties in Intel’s processors that can allow potential malicious hackers to retrieve data from CPUs.
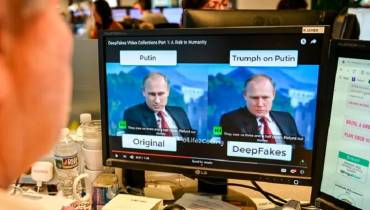
ZombieLoad, also technically known as CVE-2018-12130 as disclosed by Intel, is a chip flaw, which might result in leaking secrets. It lies in the same category of side-channel attacks as Meltdown and Spectre did back in 2018.
Researchers from the Graz University of Technology first discovered the flaw and later disclosed it to Intel. This flaw affects all the Intel chips made since 2011. As a result of this intimation, Intel has issued a code to fix this flaw which is yet to be implemented by individual manufacturers and then installed by individual users.
Intel has graded the severity of this attack as “medium”. Whereas researchers claim that, it is far more serious than stated.
Zombie Loads are huge amounts of data that a CPU cannot deal with, without crashing. These Loads come with microcode that prevents the PC from crashing. These Loads may contain sensitive data and the flaw in Intel chips may allow this information to be read by unauthorized entities.
Attack Overview
ZombieLoad itself is an offbeat category of the side-channel attacks. These invasions also referred to as data-sampling attacks, have opened a completely new field of research for the folks in academia.
ZombieLoad thrives on the fact that the fill buffer is accessible by all logical CPUs and it doesn’t recognize privileges yet. Hence putting a great amount of sensitive data at risk. Owing to the fault in Intel microchips, the data load asks for a microcode to assist it. This leads the load to sensitive information for a while before it is directed back to where it was intended to go.
Apple, Google, and Microsoft announced the availability of updates recently. Hence, ZombieLoad isn’t the kind of flaw someone is imminently at risk from.
Make sure your internet provider offers a reliable internet connection to download these updates timely. After the updates, a potential attacker won’t be able to exploit ZombieLoad remotely. They’ll have to run a code on the targeted machine to be able to access its data.
Monitoring Browsing-Behavior
ZombieLoad is capable of detecting certain byte sequences within the loaded data. For example, an unprivileged attacker, using a different machine can leverage ZombieLoad to screen a browsing session. Researchers haven’t yet confirmed any malicious activity on this flaw.
- Keyword Detection: Keyword detection lets the attacker determine the type of information a victim is consuming based on the keywords used in a certain browsing session.
- URL Recovery: In this kind of attack, hit and trial method is used to determine the domains that are repetitively visited by the victim. Hence helping the attacker learn about their browsing behavior. This kind of attack is not just restricted to web domains, but it can also lead to other predictable entries like credit-card numbers and session cookies.
“Experts say that trying to protect yourself from ZombieLoad can result in performance losses of up to 40% initially.”
How to Solve It?
ZombieLoad, as much as the authorities are downplaying it, is still a threat to sensitive information. Mitigating this issue is the need of the hour. I have listed some ways to fix this issue for each kind of operating system. I’ll keep updating the list as new solutions come out.
ZombieLoad Fix for Android Devices
Although most Android devices run on ARM hardware and will not be affected by ZombieLoad directly. However, any Android device using Intel Hardware will need to install patches issued by the hardware manufacturer.
Check their websites or Twitter to get the latest updates on the release dates of these patches.
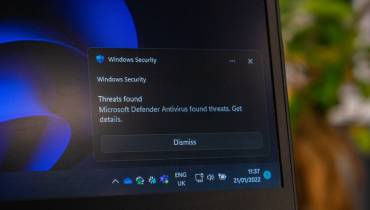
ZombieLoad Fix for Windows PCs
Windows PCs are the ones that are going to be affected the most by this attack, Including Windows 10, 7 and XP computers. On the brighter side, Microsoft has already released an update that should download automatically to your computer. However, check the latest windows update, just to be sure.
You can also download the fix from Microsoft’s support website.
ZombieLoad Fix for Mac Users
Apple has also released a patch to mitigate ZombieLoad that brought all the MacBooks, released since 2011, under threat.
However, the application of all these patches on Macs may result in a 40% fall in the performance. We really expect that Mac and Intel come to terms to reduce this performance fall to a bare minimum.
Fix ZombieLoad for Linux
Red Hat had developed security updates for products, which may result in performance issues but are capable of mitigating the bigger issue at hand. Until the time these performance issues are catered to, keep the app installed in your devices.
How to Protect Firefox and Chrome Against ZombieLoad?
Mozilla in its statement said that Firefox Beta and Firefox Nightly already have these patches installed. Whereas Google advised Chrome users to update their Operating System to avoid any inconvenience.
In short, if you are someone who is concerned about his data security, one quick solution is installing all the latest updates of your operating system. Most OS do it automatically, whereas others might require you to update manually, depending on your system settings.