How Blockchain Technology Can Bolster Your Business’ Cyber Security

Cyber-crimes have become rampant and the latest battle ground for businesses and enterprises. Whether it is a small business, healthcare system, university, government office or military base, cyber-crimes can hit any of them to steal and or damage private data.
Stolen data is used maliciously to either hack the site or extort money from people. This risk of a cyber-attack makes any ecosystem on the web quite vulnerable to breaches. In fact, the cost of malware attacks on companies is estimated to average at $2.4 million.
Because of the heightened risk of cyber-crimes today, more and more companies are investing in technology that prevents the effect and occurrence of these cyber-attacks on the web.
To combat cyber threats, IT analysts predict there will be an investment of $1 trillion in cyber security within the relatively short time span from 2020 to 2025.
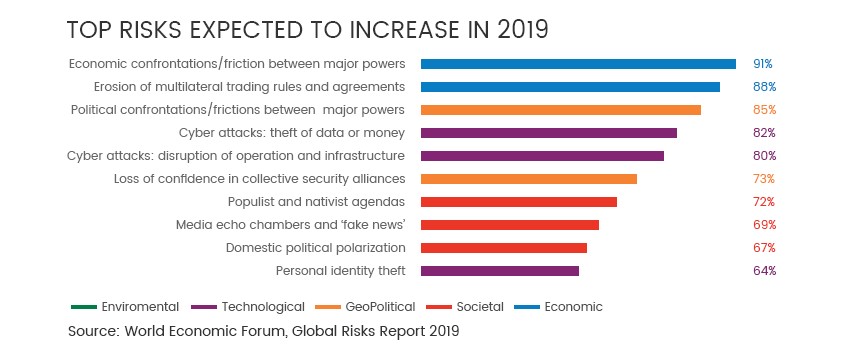
Graphic representation of top cybersecurity risks of 2019, Global Risks Report 2019.
According to the World Economic Forum’s Global Risks Report 2019, there was an 80% risk of disruption of operations and infrastructure due to cyber-attacks this year. And an 82% risk is posed by theft of data and money owing to cyber-attacks.
Reports also show that nearly 75% of CEOs prioritize investing in technologies that offer cyber-security protection. Blockchain technology is one of the revered solutions emerging that businesses are turning to for protecting their data from cyber space attacks.
Companies like IBM, General Motors and even NASA, for example, have invested in Blockchain technology to save their data and information from floating out.
Basically, Blockchain technology uses the ledger platform to distribute data in encrypted form and in pockets that are decentralized. This gives it an edge over other data distribution methods and also makes it an ideal tool for cyber security protection.
“Reports by Purplesec.us suggests that US government shells $15 billion on cyber security. 75% of CEOs of enterprises invest in cyber security technologies to avert loss of data due to threats.”
Why Blockchain technology is best for cyber security reinforcement
Tons of sensitive data enters an ecosystem like a typical eCommerce website, healthcare company and enterprises of all kinds. The data enters through IoT devices, social media platforms, cloud storage spaces and many other lose ends on the web.
Blockchain technology tightens these lose ends to ensure that there is not an atom of data being floated without encryption. This way, it nullifies risks of cyber-attacks and keeps data secure.
Let’s explore in more detail how Blockchain helps to prevent cybercrimes.
1. Blockchain offers decentralized storage
The idea of storing data in one place or in single cloud or single server makes its vulnerable to cyber-attack. The hacker just needs to break the security of that one area and grab all data stored there. This is easily ruled out by using Blockchain based storage solutions, which stores data in archived form at different locations. The access is only through cryptographic access key, which can be easily revoked when sensed with a threat.
This way, hackers cannot enjoy a single point entry and data is stored safely in Blockchain repositories scattered across the internet. According to a report by Symantec, cryptojacking reduced by more than half (52%) due to the use of crypto currency offered by Blockchain. This is a grand success that blocked ransomware and minimized cybercrime.
2. Blockchain blocks IoT data exchanges upon threat suspicion
Hackers generally hack the basic devices that connect systems. Be it routers, switches, cameras, thermostats or nodes, they are all vulnerable to threats. Statistics suggest that 90% of the cyber-attacks is actually due to infected devices connected by IoT.
Hackers can easily access the credentials and data floating between these devices and execute their malicious plan. But, by using Blockchain, data exchange between these various devices can be stopped based on a suspicion of something amiss. With Blockchain, your devices can be designed to form networks that stop any node that behaves abnormally.
Timely communication between remote devices to pass the message of threat is possible through Blockchain. By creating a decentralized flow of data, it makes it really tough for a hacker to crack in. Its next to impossible to break such high level of security that can quickly block nodes and not give permission for data exchange.
Thus, your Internet of Things (IoT) systems are safer with Blockchain.
3. Blockchain addresses vulnerability of DomainName Servers (DNS)
DNS are centralized, making them open to threats. Hackers can easily plan as well as execute attacks by breaking the connection between website name and IP address.
There have been instances where visitors were routed to scam websites by breaking this connection. In such cases, visitors can be put in infinite loops until the website owners and administrators yield and pay a certain amount to get out of the attack.
These kinds of attacks can be mitigated with the help of tail log files, which detect and report suspicious activity early on. However, it is a long process and needs to be monitored actively. With Blockchain, though, the domain information is stored in an encrypted form on a distributed ledger giving no room of access.
This way, Blockchain protects DNS by preventing a breach in the first place, making the entire DNS system a lot more secure than those protected with tail log files.
4. Blockchain secures private messages
A huge amount of malicious software has been known to target data floated on social media sites, public websites, twitter handles and other platforms with public interaction. And eCommerce is perhaps the most undefended platform in this regard.
Meta data is extracted from eCommerce customers to know their preference, shopping behavior and design better marketing jigs to increase sales. Even now, there are many apps that lack adequate mechanism to encrypt cross messenger dialogue.
Blockchain adds a layer of security by encrypting all messages and securing every node shared online, including those associated with different platforms. By using decentralization, it keeps the data safe and still connects the social media platforms. This way, Blockchain helps in securing flow of data from one online platform to another.
Conclusion
There are many more ways and levels where Blockchain technology can be used to impart security to online systems. Many companies are now already becoming aware of this often-underutilized trump card and are investing in it.
Companies like IBM has reportedly invested $200 million in Blockchain, and other tech and financial firms are making big investments in Blockchain technology too. Collectively, experts predict $2.1 billion of investment will be spent in this technology.
These stats prove that Blockchain is making its mark in the realm of cyber security and slowly enveloping enterprises and data flow points on the internet. You should probably jump onboard to protect your business and data from malicious cyber-attacks with Blockchain tech.



![9 Tips for Managing Your Online Writing Projects Efficiently [node:titile]](/sites/default/files/styles/thumbnail_rectangle/public/open-book-laptop-online-writing-tips.jpeg?itok=iq4PIT7b)